Unlike PGP, Speak Freely is a conventional secret key cryptographic system. Why? Because the RSA public key cryptosystem is the subject of U.S. Patent 4,405,929 and I have no desire to thread through the legal maze that PGP had to run in order to become both legal and freely available. Rather than replicating the public key functionality of PGP, Speak Freely cooperates with a copy of PGP installed on your machine, delegating the public key encryption of a session key to PGP. If you have PGP installed on your machine, please turn to the section on PGP key exchange. Users without access to PGP or who, for some reason or another, can't execute PGP from within Speak Freely can use the following technique to generate and exchange session keys.
First of all, make up a key. You could pick a long nonsense phrase like,
The fribbits seem glinky today, don't you think?
or some gibberish pounding on the keyboard. (But watch out! That's often a lot less random that you might think. That's how the Russians used to make one-time pads for spies. The alternation of left and right hand keystrokes on mechanical typewriters was clearly evident from captured pads.)
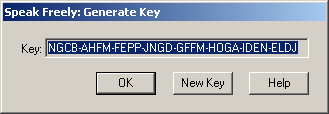
But why go to the trouble when Speak Freely will make up a key for you on the spot? The Options/Create Key menu item computes a seed value from the time, date, and a variety of information about your computer and uses it to generate a hash code using the MD5 algorithm. The key is displayed in a dialogue box:

Each time you press the "New Key" button, another key is generated, containing 128 bits of information, the same as an AES, Blowfish, or IDEA key and more than twice the 56 bits of a DES key. The text of the key is automatically selected and may be copied to the clipboard with Ctrl+C and pasted into a key field in the Options/Connection dialogue box and an electronic mail message to the person you want to speak with. The message might read something like:
Hi! I'd like to talk to you around 21:00 your time tonight with Speak Freely. I've generated a key of:
NHCG-AJHP-ILJN-DHAI-NFEI-CPKO-PINJ-JIAA for this conversation. Please paste this key into the IDEA encryption box when you set up the connection to my machine. I'm looking forward to chatting with you!
Encrypt the message with whatever tool you use to protect your electronic mail, and send it winging its way over the Internet.
When your friend receives the message and decrypts it, she will know the key to use for your forthcoming conversation. You can either generate a new random key for each conversation (as PGP does) or, if you trust the other person (and yourself!) to keep the key secret, use it for multiple conversations with that individual.
If you use a public key cryptosystem, this technique permits you to exchange keys for conversations with people you've never previously communicated with in any manner, as long as you trust their published public keys to actually be theirs. Of course when you let Speak Freely generate the key, you're trusting me to not have installed a "back door" that allows me to know what key you'll get, or to have accidentally introduced a bug which makes the keys predictable.